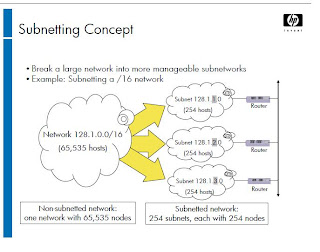
ni nak share tentang ip addres..macamana proses dari private IP ke public IP

These organizations, in turn, allocate blocks of public Internet IP addresses to corporations and Internet Service Providers. Check with your local IT department or ISP to obtain an address on the public Internet.Connecting to a private Intranet with an Internet Address Many organizations choose not to connect individual hosts directly to the public Internet for security reasons. Why expose your hosts to thousands of hackers, if those hosts need only limited access to the outside networks? Instead, many organizations choose to configure a private Intranet that is insulated from the dangers of the public Internet by some sort of network firewall. Firewalls can be used to control the type of traffic that passes both in and out of your organization's private Intranet.There are two ways to obtain and allocate IP addresses in this situation. One approach is to request a public Internet IP address for each host, then shield those hosts behind your firewall. If you choose to go this route, you will have to apply for a block of unique, public Internet addresses from your ISP or the websites listed in the previous section.
Connecting to a private Intranet Using Network Address TranslationSince public Internet IP addresses are in short supply, many organizations choose instead to provide Internet access to their internal hosts using some sort of proxy server software,which does not require a unique Internet address for every host on the private Intranet. Using this approach, hosts on your private Intranet are assigned addresses from the following
blocks of IPs:
10.*.*.*
172.16-31.*.*
192.168.*.*
These addresses are designated specifically for use on private Intranets. Hosts with
addresses within these ranges may not be connected directly to the public Internet, nor are packets destined for these addresses allowed to pass on or through the public Internet. Since these addresses are not allowed directly on the public Internet, any organization may use these addresses without fear of conflicting with other organization's addresses.
Question: If packets destined for these addresses are not allowed on the public Internet, how can these hosts send email or access web sites outside their private networks?
Intranet hosts that need web access to the outside world may access the Internet via a proxy server. These hosts can be configured to relay all external web access requests through a specially configured server with connections both to the private Intranet, and the public Internet. The proxy server forwards internal clients' access requests to external sites via its IP address on the public Internet, then relays the responses back to the requesting clients. Email service may be provided using similar functionality. Hosts on the private Intranet send and receive email via a specially configured Mail Gateway that straddles both the private Intranet, and the public Internet.