ni adalah cara - cara nak lajukan internet
1.pastikan komp. tiade virus--->update antivirus dan scan.
2.pastikan tiada juga spyware,malware...dan sebagainya "kebanyakkan antivirus tidak dapat mengesan spyware2 ni secara meluas---> so install anti-spyware update dan scan.
3.disable servis2 yang tidak berguna "kalau was2 boleh check dekat www.blackviper.com"
4.untick startup di msconfig yang x berguna.
5.update driver2 yg digunakan.--->boleh guna software seperti everest ultimate untuk download driver.(ni key untuk version 5.3 C3MDF-TEN47-L64AT-Y4PUF-J73VQ
6.buka gpedit.msc-->administrative template-->network-->qos packet scheduler-->klik limit reservable bandwitch-->enable-->tukar nilainya ke 0--->apply.
7.setting yg biasa aku buat dekat registry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RemoteComputer\NameSpace
del key ni {D6277990-4C6A-11CF-8D87-00AA0060F5BF} dan {2227A280-3AEA-1069-A2DE-08002B30309D}
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\ClearPageFileAtShutdown
klik clearpagefileatshutdown nilai dia letak 1.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\DisablePagingExecutive
klik disablepagingexecutive nilai tukar 1.
8.kalau guna windows xp boleh cari tool ni-->winsock fix
selamat mencuba
Tuesday, May 24, 2011
Sunday, May 22, 2011
cara nak buang viru s sality
virus sality memang susah nak remove sebab dia disable fungsi
security centre
antivirus
firewall
hidden file
ni satu cara yang aku dapat.download tools kat web sini
security centre
antivirus
firewall
hidden file
ni satu cara yang aku dapat.download tools kat web sini
Sunday, May 15, 2011
IDSafe: Basic Identity Protction
Everyone is at risk for America’s fastest-growing crime – identity theft – so we believe that everyone should have protection – for free. That’s why we loaded up IDSafe with valuable protection for your identity and credit
Todays world not only America but whole world is targeted. IDSafe provides consumers a free credit score updated monthly and Facebook social networking privacy risk monitoring. In addition, continuous monitoring of known online black market venues where identity thieves buy and sell consumers’ personal information is included to prevent IDSafe users’ vital data from falling into the wrong hands
With no subscription time limit or purchase requirement, IDSafe provides the absolute best value for core protections that everyone should have in place,” Mitic said. “And, should you ever decide to deepen or broaden your protection, IDSafe customers will have easy access to an array of additional protections from TrustedID’s award-winning premium services to add comprehensive credit monitoring, online credit reports and more.
Todays world not only America but whole world is targeted. IDSafe provides consumers a free credit score updated monthly and Facebook social networking privacy risk monitoring. In addition, continuous monitoring of known online black market venues where identity thieves buy and sell consumers’ personal information is included to prevent IDSafe users’ vital data from falling into the wrong hands
With no subscription time limit or purchase requirement, IDSafe provides the absolute best value for core protections that everyone should have in place,” Mitic said. “And, should you ever decide to deepen or broaden your protection, IDSafe customers will have easy access to an array of additional protections from TrustedID’s award-winning premium services to add comprehensive credit monitoring, online credit reports and more.
Tuesday, May 10, 2011
Buat mirroring port
ni nak share sikit cmano nak buek mirroring port kat switch.ni gune switch 3com 4200G tapi mungkin model switch atas yang den gun0 mungkin command die berbeza sedikit,,
4500> system-view
[4500] interface Ethernet 1/0/1
[4500-Ethernet1/0/1] mirroring-port ?
both Mirror the inbound and outbound packets of the interface
inbound Mirror the inbound packets of the interface
outbound Mirror the outbound packets of the interface
[4500-Ethernet1/0/1] mirroring-port both
[4500-Ethernet1/0/1] quit
[4500] interface GigabitEthernet 1/0/27
[4500-GigabitEthernet1/0/27] monitor-port
[4500-GigabitEthernet1/0/27] quit
[4500] display mirror
Monitor-port:
GigabitEthernet1/0/27
Mirroring-port:
Ethernet1/0/1 both
=============================================================
seandainye tak boleh buat monitor-port.sbb die bagitau STP enable, kite disable kan dulu
system
System View: return to User View with Ctrl+Z.
[4500G]interface GigabitEthernet1/0/16
[4500G]-GigabitEthernet1/0/16]stp disable
[4500G]-GigabitEthernet1/0/16]stp edged-port disable
[4500G]-GigabitEthernet1/0/16]quit
bila dah siap kita save kan die
pastu bile nak tgk balik
[4200G]display mirroring-group all
mirroring-group 1:
type: local
status: active
mirroring port:
GigabitEthernet1/0/5 both
monitor port: GigabitEthernet1/0/16
selamat mencuba
4500> system-view
[4500] interface Ethernet 1/0/1
[4500-Ethernet1/0/1] mirroring-port ?
both Mirror the inbound and outbound packets of the interface
inbound Mirror the inbound packets of the interface
outbound Mirror the outbound packets of the interface
[4500-Ethernet1/0/1] mirroring-port both
[4500-Ethernet1/0/1] quit
[4500] interface GigabitEthernet 1/0/27
[4500-GigabitEthernet1/0/27] monitor-port
[4500-GigabitEthernet1/0/27] quit
[4500] display mirror
Monitor-port:
GigabitEthernet1/0/27
Mirroring-port:
Ethernet1/0/1 both
=============================================================
seandainye tak boleh buat monitor-port.sbb die bagitau STP enable, kite disable kan dulu
System View: return to User View with Ctrl+Z.
[4500G]interface GigabitEthernet1/0/16
[4500G]-GigabitEthernet1/0/16]stp disable
[4500G]-GigabitEthernet1/0/16]stp edged-port disable
[4500G]-GigabitEthernet1/0/16]quit
bila dah siap kita save kan die
pastu bile nak tgk balik
[4200G]display mirroring-group all
mirroring-group 1:
type: local
status: active
mirroring port:
GigabitEthernet1/0/5 both
monitor port: GigabitEthernet1/0/16
selamat mencuba
Monday, May 9, 2011
Anti-Hacker.Toolkit.3rd.Ed.ebook-Spy
Thursday, May 5, 2011
Subnetting Concept
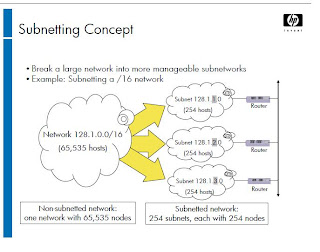
Subnetting makes it possible to divide a large network IP address space into several smaller,more manageable "subnets."
The example on the slide shows a subnetted /16 network. Without subnetting, the 128.1.0.0/16 network would have 65 thousand hosts on the same physical network, which could easily lead to excessive collisions
This network, however, has been subdivided into 254 subnets. Each of these subnets could potentially have up to 254 hosts.
Subnet Addresses
----------------
128.1.1.0
128.1.2.0
...
128.1.253.0
128.1.254.0
Subnets are separated from one another by routers, which overcome both the collision and topological issues discussed on the previous slide.
Subnetting also makes it easy for the network administrator to delegate authority for
portions of the IP network address space to other entities within the organization. Simply assign each department a separate subnet. Each network administrator then becomes responsible for a subnet within the larger corporate network
Limitations of Large Networks

Although a /8 network address allows for 16 million host addresses, in reality, it is impractical to have that many hosts sharing a single physical network
Topological Limitations
Many LAN topologies don't allow 16 million nodes on a single physical network.Excessive Collisions If any two nodes on an ethernet network transmit at the same instant, a collision results and both nodes must attempt to retransmit. As the number of nodes on the network increases,the likelihood of collisions increases as well.Administrative Challenges Simply keeping track of who has which IP address in a 16- million node network would be an administrative challenge for even the best network administrator.Poor Network Performance All of these issues result in degraded network performance as more and more hosts compete for limited bandwidth on a network
Excessive Collisions
If any two nodes on an ethernet network transmit at the same instant, a collision results and both nodes must attempt to retransmit. As the number of nodes on the network increases,the likelihood of collisions increases as well
Administrative Challenges
Simply keeping track of who has which IP address in a 16- million node network would mbe an administrative challenge for even the best network administrator
Poor Network Performance
All of these issues result in degraded network performance as more and more hosts compete for limited bandwidth on a network.
Obtaining an IP Address
ni nak share tentang ip addres..macamana proses dari private IP ke public IP

These organizations, in turn, allocate blocks of public Internet IP addresses to corporations and Internet Service Providers. Check with your local IT department or ISP to obtain an address on the public Internet.Connecting to a private Intranet with an Internet Address Many organizations choose not to connect individual hosts directly to the public Internet for security reasons. Why expose your hosts to thousands of hackers, if those hosts need only limited access to the outside networks? Instead, many organizations choose to configure a private Intranet that is insulated from the dangers of the public Internet by some sort of network firewall. Firewalls can be used to control the type of traffic that passes both in and out of your organization's private Intranet.There are two ways to obtain and allocate IP addresses in this situation. One approach is to request a public Internet IP address for each host, then shield those hosts behind your firewall. If you choose to go this route, you will have to apply for a block of unique, public Internet addresses from your ISP or the websites listed in the previous section.
Connecting to a private Intranet Using Network Address Translation
Since public Internet IP addresses are in short supply, many organizations choose instead to provide Internet access to their internal hosts using some sort of proxy server software,which does not require a unique Internet address for every host on the private Intranet. Using this approach, hosts on your private Intranet are assigned addresses from the following
blocks of IPs:
10.*.*.*
172.16-31.*.*
192.168.*.*
These addresses are designated specifically for use on private Intranets. Hosts with
addresses within these ranges may not be connected directly to the public Internet, nor are packets destined for these addresses allowed to pass on or through the public Internet. Since these addresses are not allowed directly on the public Internet, any organization may use these addresses without fear of conflicting with other organization's addresses.
Question: If packets destined for these addresses are not allowed on the public Internet, how can these hosts send email or access web sites outside their private networks?
Intranet hosts that need web access to the outside world may access the Internet via a proxy server. These hosts can be configured to relay all external web access requests through a specially configured server with connections both to the private Intranet, and the public Internet. The proxy server forwards internal clients' access requests to external sites via its IP address on the public Internet, then relays the responses back to the requesting clients. Email service may be provided using similar functionality. Hosts on the private Intranet send and receive email via a specially configured Mail Gateway that straddles both the private Intranet, and the public Internet.

These organizations, in turn, allocate blocks of public Internet IP addresses to corporations and Internet Service Providers. Check with your local IT department or ISP to obtain an address on the public Internet.Connecting to a private Intranet with an Internet Address Many organizations choose not to connect individual hosts directly to the public Internet for security reasons. Why expose your hosts to thousands of hackers, if those hosts need only limited access to the outside networks? Instead, many organizations choose to configure a private Intranet that is insulated from the dangers of the public Internet by some sort of network firewall. Firewalls can be used to control the type of traffic that passes both in and out of your organization's private Intranet.There are two ways to obtain and allocate IP addresses in this situation. One approach is to request a public Internet IP address for each host, then shield those hosts behind your firewall. If you choose to go this route, you will have to apply for a block of unique, public Internet addresses from your ISP or the websites listed in the previous section.
Connecting to a private Intranet Using Network Address Translation
Since public Internet IP addresses are in short supply, many organizations choose instead to provide Internet access to their internal hosts using some sort of proxy server software,which does not require a unique Internet address for every host on the private Intranet. Using this approach, hosts on your private Intranet are assigned addresses from the following
blocks of IPs:
10.*.*.*
172.16-31.*.*
192.168.*.*
These addresses are designated specifically for use on private Intranets. Hosts with
addresses within these ranges may not be connected directly to the public Internet, nor are packets destined for these addresses allowed to pass on or through the public Internet. Since these addresses are not allowed directly on the public Internet, any organization may use these addresses without fear of conflicting with other organization's addresses.
Question: If packets destined for these addresses are not allowed on the public Internet, how can these hosts send email or access web sites outside their private networks?
Intranet hosts that need web access to the outside world may access the Internet via a proxy server. These hosts can be configured to relay all external web access requests through a specially configured server with connections both to the private Intranet, and the public Internet. The proxy server forwards internal clients' access requests to external sites via its IP address on the public Internet, then relays the responses back to the requesting clients. Email service may be provided using similar functionality. Hosts on the private Intranet send and receive email via a specially configured Mail Gateway that straddles both the private Intranet, and the public Internet.
BROADCAST
Subscribe to:
Posts (Atom)



